Trends in Cybersecurity
2023 Trends in Cybersecurity Increased use of cloud services: The adoption of cloud services has increased significantly in recent years, and this has resulted in a rise in cloud-related cyber…
Read MoreYour Company Is Only as Strong as Your Weakest Password
With constantly-escalating security threats, the value of a strong password cannot be overemphasized. However, what many businesses fail to realize is that their security systems are only as robust as…
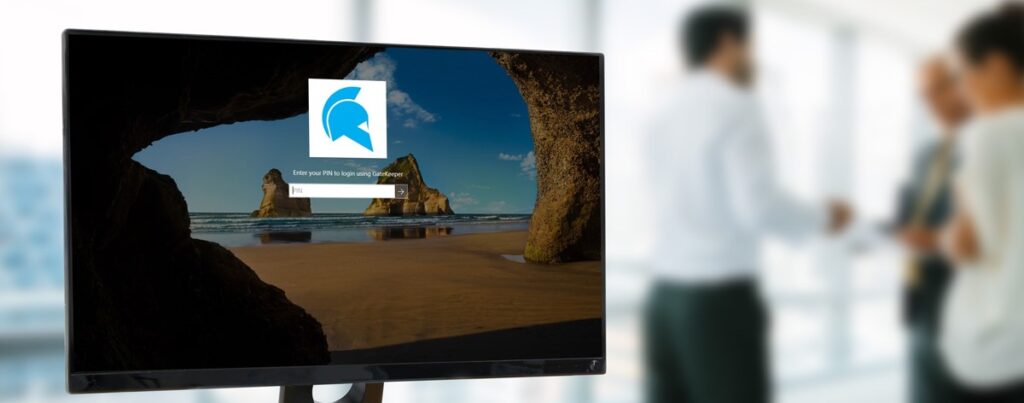
Read MoreAdvanced Screen Lock Software Solution for Enterprise – GateKeeper Proximity
A Paradigm Shift in Enterprise Security In the face of an unprecedented increase in cyber threats, traditional screen lock methods are woefully inadequate for enterprises. According to Verizon’s 2020 Data…
Read MorePasswords for Healthcare Providers
Passwords in the healthcare workplace actually cost more to maintain and deal with than other industries. Clinicians need faster and more seamless access to records and PCs. It takes too…
Read MorePassword Lifecycle Management
The need for robust password lifecycle management has become more critical than ever. Weak or compromised passwords can be exploited by cybercriminals, leading to data breaches and significant financial losses…
Read MoreSmart Access Control for PCs
Smart access control is becoming increasingly important as the need for secure access to personal computers (PCs) grows. With the rise of remote work, cyber attacks, and data breaches, it’s…
Read More2FA Using a Proximity Beacon.
The constant evolution of cyber threats has made it more imperative than ever for organizations to adopt multi-layered security measures. One widely adopted method is two-factor authentication (2FA), a system…
Read MoreRemoving Passwords in Senior Care Communities for Simpler Logins
We need to remove passwords from the equation – they slow the whole process down. While technology can undoubtedly enhance care quality and operational efficiency, it also presents unique challenges…
Read MoreMotivate Users to Use Strong Passwords
The security of personal and sensitive information is of utmost importance. However, despite the importance of strong passwords, many users continue to use weak and easily guessable passwords, putting their…
Read More