What is Continuous Authentication?
Continuous Authentication explained. Continuous authentication/continuous 2FA is an advanced method of identity verification. This mechanism runs the authentication protocol an ongoing basis from the start of a session to the…
Prevent Password Problems
Playing the password game isn’t hard – but winning at it is like playing chess with no way to checkmate the opponent. That’s going to cause a lot of password…
Seamless MDT Login with Auto-Lock for Patrol Cars
Compliance requirements for law enforcement’s MDTs are getting stricter and requires a solution that meets the needs of both the user’s ease-of-use and the IT team’s need for stronger security.…
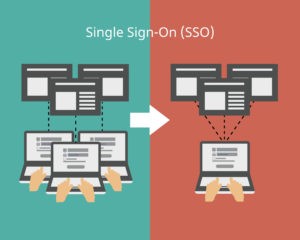
How Single Sign-on Works
SSO (single sign-on) is an authentication mechanism that allows users to login once using a single login account to access multiple applications or websites without re-entering the same login credentials.…
Shared Clinical Workstation Security and Access
Clinical computers are usually shared chaotically between clinicians and present unique vulnerabilities for IT teams in the healthcare ecosystem. The shared clinical workstation is used by physicians for nearly everything:…
See Who is Logging in on Shared Windows Accounts
Need to accurately audit access logs across the network due to a shared computer? Not easy to track who is logging in when to which computer? Usually, admins can go…
Benefits of Hardware Tokens for Authentication
IT administrators have many responsibilities that require elevated access to the systems that they are responsible for maintaining. This makes them attractive targets for attackers looking to penetrate the most…
What’s my computer’s domain name?
Look up your Computer’s Domain Name on Windows 10 PC. Windows 10: To find the Domain name for your Windows 10 PC, please follow the directions below. Click on the Start Menu.…
Improving Patient Care by Reducing IT Burdens on Physicians
The words condemning the inefficiencies and excessive administrative tasks of the current electronic health record (EHR) system came directly from the American College of Physicians (ACP). They called it “inefficient,…