Access control is the selective process of granting or denying permission to gain access to system (e.g. a computer, data) or a physical location (door, office, building).
Active Directory (AD) is a directory service for Windows domain networks. AD is responsible for authenticating and authorizing users on the network.
Adaptive authentication is a context-aware approach that tailors login requirements based on risk signals like device, location, and behavior. It helps prevent unauthorized access while minimizing friction for trusted users. By dynamically adjusting security measures, it supports both strong protection and a smooth user experience.
An Advanced Persistent Threat (“APT”) is a cyber attack in which a team of intruders use continuous, sophisticated hacking techniques to establish a long-term presence on a network, intending to breach highly sensitive data.
AES-256 encryption is a standard U.S. block cipher algorithm for protecting (encrypting) data at rest.
Agentic AI is a form of artificial intelligence that acts autonomously, setting goals and making decisions without constant human input. Unlike traditional AI, it can initiate actions based on context and adapt over time. This emerging approach is reshaping how systems respond to users, manage risk, and operate in dynamic environments.
Artificial Intelligence (AI) refers to the ability of machines to perform tasks that normally require human intelligence. These include recognizing patterns, making decisions, and learning from data. AI is widely used across industries to improve efficiency, enhance user experiences, and support real-time automation.
An Air Gap System refers to a security measure that involves physically isolating a computer or network from unsecured networks, including the public internet or any other external network. This isolation, often literal, with no network cables or wireless connections, creates a “gap of air” between the secure system and potential external threats.
Anti-Virus Solution is software designed to recognize and protect against malware infections and unauthorized access of digital data. They are an essential component in a good cybersecurity system, as they safeguard against many popular forms of cyber attacks, which may include ransomware, spyware, or trojans.
The attack surface is the sum of all possible attack directions ("attack vectors") in an environment. There are two types of attack surfaces: physical and digital.
Auditability refers to the ability of a system, process, or organization to be audited—that is, reviewed and verified—through the presence of accurate, complete, and accessible records. It ensures that actions, decisions, and changes within a system can be traced and independently evaluated to confirm compliance with policies, regulations, and performance standards.
Auditing refers to the process of evaluating the process and systems of an organization's IT infrastructure to determine effectiveness, security, and efficiency. This empowers companies to take targeted, preemptive action in properly strengthening their IT processes and operations.
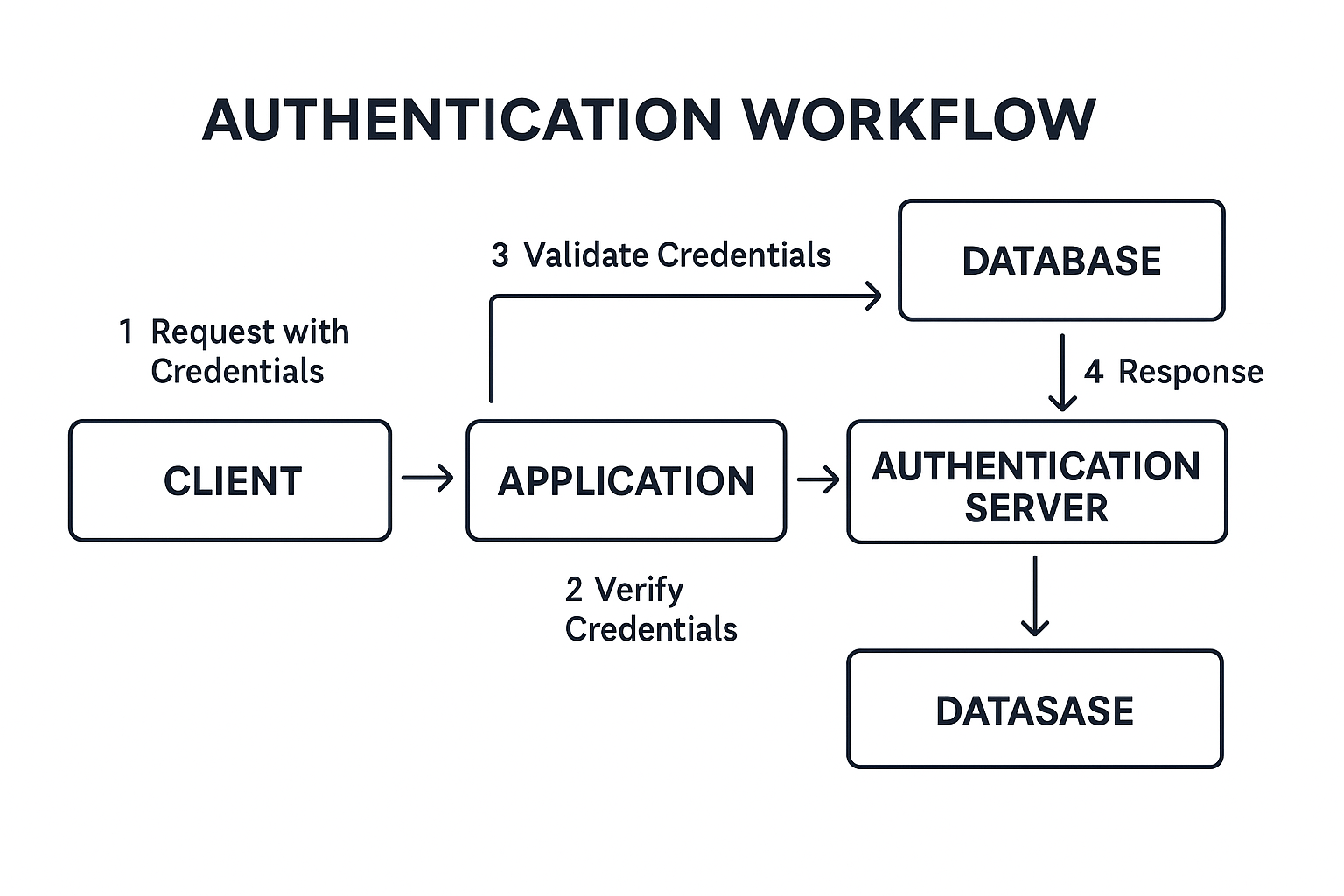
An authentication workflow is a series of steps that verify a user's identity before granting access to a system or application. It involves the exchange of credentials, such as usernames and passwords, tokens, or biometric data, between the user and the authentication system.
Awareness Training is a formal process used to educate individuals on security risks, responsibilities, and best practices related to their role in protecting information systems and sensitive data.
According to studies, over 30% of all support tickets are related to password resets/forgotten passwords.
Enterprise 2FA and password manager. One key for all your passwords. Experience fully automated login and security. For example, faster MFA, auto-OTP, password manager, and worry-free workflow with proximity-based privileged access management for Windows 11, 10, 8, 7, VPNs, websites, and desktop applications including MES, EHR, CAD, and more. Overall, a massive upgrade to security and efficiency.
or call 240-547-5446