Why Enterprises Should Rush to Adopt Multifactor Authentication.
Phishing attacks, social engineering, database breaches, cyber attacks – all terms that have found their way into our daily lives. If the incessant news of the past decade has shown any trend, it’s that no organization is immune to cyberattacks. And a lot of this evidence points to single points of failures – passwords. Adopt multifactor authentication if you have not already done so.
You’re an IT manager for 500 employees who were all working out of your office earlier this year. When working at the office, there might have been a parking gate to pass through, a lobby with a security guard, turnstile to swipe in at, and maybe another door to swipe past before employees got to your workstation. There’s probably a few other security measures like CCTV cameras and even security-conscious colleagues to help keep cybersecurity hygiene strong. But when it comes to data access, a majority of the organizations still depend on their employees using simple passwords to access their digital assets. This cavalier attitude towards computer security is one of the largest threat vectors for any organization. But interestingly the easiest to solve using multi-factor authentication.
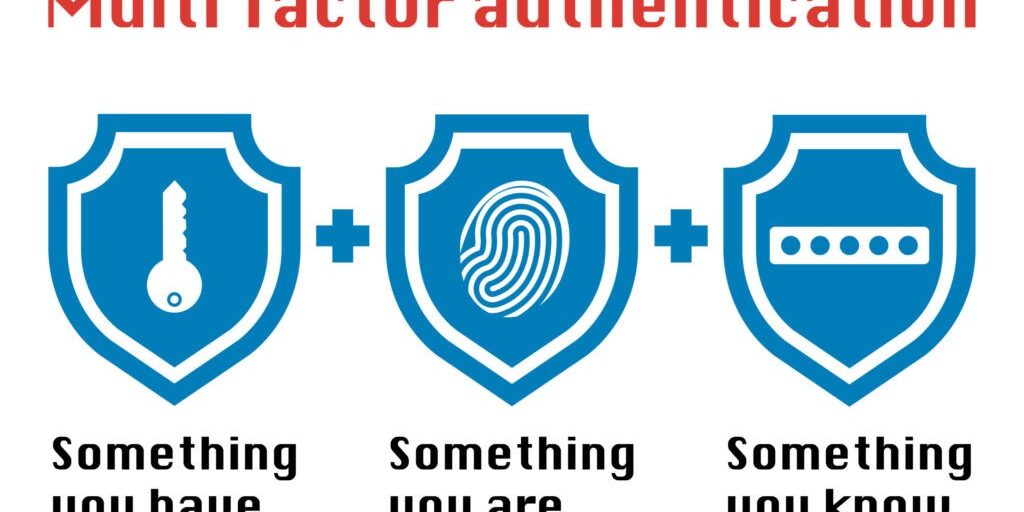
Though MFA has been available for years, its popularity (and necessity) has skyrocketed due to the rise of pandemic. MFA means you need two or more pieces of authentication than just your username and password combo (e.g. your smartphone, hardware token, or biometric signature). With the largest increase in remote workforce numbers, it is essential that enterprises have defense mechanisms in place to tackle the new situation. What security staff thought was a vulnerable cybersecurity infrastructure a year ago is made exponentially worse today. The point of MFA is to add additional layers of security in case one layer is breached (password).
What if you don’t use MFA?
The first problem with not using MFA is that the potential damage from minor problems becomes major. Think of how many employees are being cavalier or downright negligent with their password security duties. MFA is like requiring two forms of ID rather than one. This is so that even if a criminal forged one form of ID, it would be very difficult to forge two or more. Forging more IDs becomes very cost-prohibitive. People aren’t in the office under watch. Admins can’t trust people while they’re at home or their local coffee shop. So the only alternative is to enforce automated security including MFA. Adopt multifactor authentication now before it’s too late.

People will share passwords
Sharing passwords doesn’t involve a daring criminal – it’s just when one user willingly shares their credentials with another person. The risk is that the person that had the password shared with them can be careless and write it down or re-share it – this is where the big risks of sharing passwords occur. MFA helps combat the risk from user sharing passwords. If the user has text OTP as a 2nd factor set up, then another user who has the shared password that logs in will have to also get the OTP that can only be obtained through the original owner’s phone, preventing the second user from logging in.
Reusing the same password
Reusing passwords leaves accounts vulnerable to credential stuffing attacks. If a cybercriminal was able to crack your email login and you use the same username and password for other accounts, then you just did the cybercriminal’s job for them. If you have MFA in place, then even with 100 compromised passwords, the criminal will require 100 2nd factors. How can admins trust users who have an inherent interest in productivity (but not directly security) to choose longer passwords that are more prone to typing mistakes? They can’t.
Increased susceptibility to phishing attacks
MFA can help combat most phishing attacks. Even if the malicious actor were to gain knowledge of a victim’s username and password (factor 1), they would still need the victim’s 2nd or even third factor to gain access. If a user receives a malicious email to login to a supposed banking site, if the user falls for this trick and gives up their login information, MFA will still guard against unauthorized access because the attacker still needs the next factor. The second factor can’t be stolen through the phishing form. Make sure employees are aware and trained for common cyber threats.
MFA options for enterprises.
Text SMS is one of the most popular forms of MFA since most people have a smartphone and is used to texting, but this method is also one of the most susceptible to cyber attacks. Spoofing attacks have proven effective at intercepting text messages. This is because texting wasn’t built with security in mind.
Hardware and software tokens are a strong choice for MFA since hackers would have to actually steal these devices. This makes the attack surface drastically smaller, making it harder for cybercriminals to penetrate. Some tokens require the user to plug into the USB port, others require reading the OTP off of the token’s LCD screen, and some are automatic. Software tokens are digital versions of tokens stored on devices such as the user’s smartphone.
Biometrics in the form of fingerprint, retina, facial, vein, and body movement are popular options to use as additional factors. The problem with biometrics is that immutability comes into play if the biometric data was ever compromised (one can’t make a new fingerprint or face once stolen). There are multiple methods attackers use to try to steal biometric information. Even scanning your Facebook profile pictures to steal facial biometric data is a real threat today.
Summary – Adopt Multifactor Authentication
Multi-factor authentication is the need of the hour. When we’re done on a computer and on websites, organizations must enforce policies to protect access to digital assets. With the plethora of MFA options available, consider your users’ needs and workflows. If organizations have to comply with certain standards like HIPAA then MFA is a requirement, and not an option anymore. Protecting the organization’s data, and more importantly, their customer’s data should be the highest priority of any security architecture. MFA goes a long way towards that goal, and must be part of any organization’s security plan going forward. Find out more about how continuous MFA works.
Finally, see GateKeeper Enterprise advanced MFA in action.
Take a self-guided tour of how you can evolve from passwords. Then you're really saving time with automation.




