Continuous and Convenient 2FA
We all use some form of authentication—passwords, passcodes, an ID card—upon entering into a place with restricted access. Whether this place is digital or real-world, authentication systems are typically founded on a barrier. This is a point of access where you must prove that you have permission before you proceed. But since so many of these barriers have been compromised in recent years, a new form of authentication could be revolutionizing security. It does this by destroying the notion of the barrier in the first place. We don’t just need solid 2FA, but also convenient 2FA.
Continuous authentication explained.
Continuous authentication is a form of digital security that, just as it sounds, ensures continuous security throughout a computing session. While traditional authentication has a high measure of confidence for authentication at the beginning of a session, the authentication may decay as that session goes on. This can happen due to a number of events. For example, “a user might walk away from his desktop computer briefly and someone else takes over the session, or malware infecting the system can take over as well,” according to CSO.
As Frank Dickson, a research director at International Data Corp. (IDC) Security Products, says “continuous authentication is a form of dynamic, risk-based authentication, [which] changes the perspective of authentication from an event to a process.” An event like walking away from your computer would leave a traditional authentication system open to threats, but continuous authentication, because it is a process, will continue to protect you.
Behavior factor in continuous authentication.
Most continuous authentication security is a form of user behavior analytics, a process of analyzing the way that an individual interacts with a device and using that information as a method of authentication. Though continuous authentication security is new, some forms are already seeking to have systems identify individuals through their key movements on a device. In this way, the system could identify whether the user of the device is the individual that can access to such information. Google’s “I’m not a robot” replacement for CAPTCHA tests is an example of such a system.
Continuous authentication is just beginning to develop and take off, but it is thought that the sector will grow exponentially. IDC released a report October 2016 predicting worldwide security spending through 2020, and “the research firm notes that user behavior analytics software will be one of the fastest growing segments of the security products market.” In 2018, continuous authenticity products may become mainstream, say CSO. Jason Chaiken, president of Vkansee, suggests some of the future uses of continuous authentication security like biometrics might be used in mobile devices, in banking, in hospitals, and on college campuses.
Supercharge security and streamline logins with convenient 2FA.
Continuous authentication is a valuable access control solution for two reasons. First, it creates a higher level of security. This type of authentication fills a gap in security that is based on an initial barrier, like passwords and 2FA. As Richard Walters, SVP of security products at Intermedia, says “it’s unlikely that employees will ever rid themselves of the bad habit of device and password sharing – a recent survey shows 46% of respondents share logins with multiple users.” Continuous authenticity solves this problem by viewing authentication as a continuous process, protecting you from other users on your devices. Read about some of the common ways hackers are trying to gain access to your desktop.
Second, continuous authentication provides a viable solution because it is convenient for the user. As biometrics systems improve, systems that measure behavioral analytics—like the movements, location, or other habits of the user—will become perfected. This method will provide a high level of security without any additional action on the part of the user.
A continuous authentication system like GateKeeper can offer you both convenience and a higher sense of security.
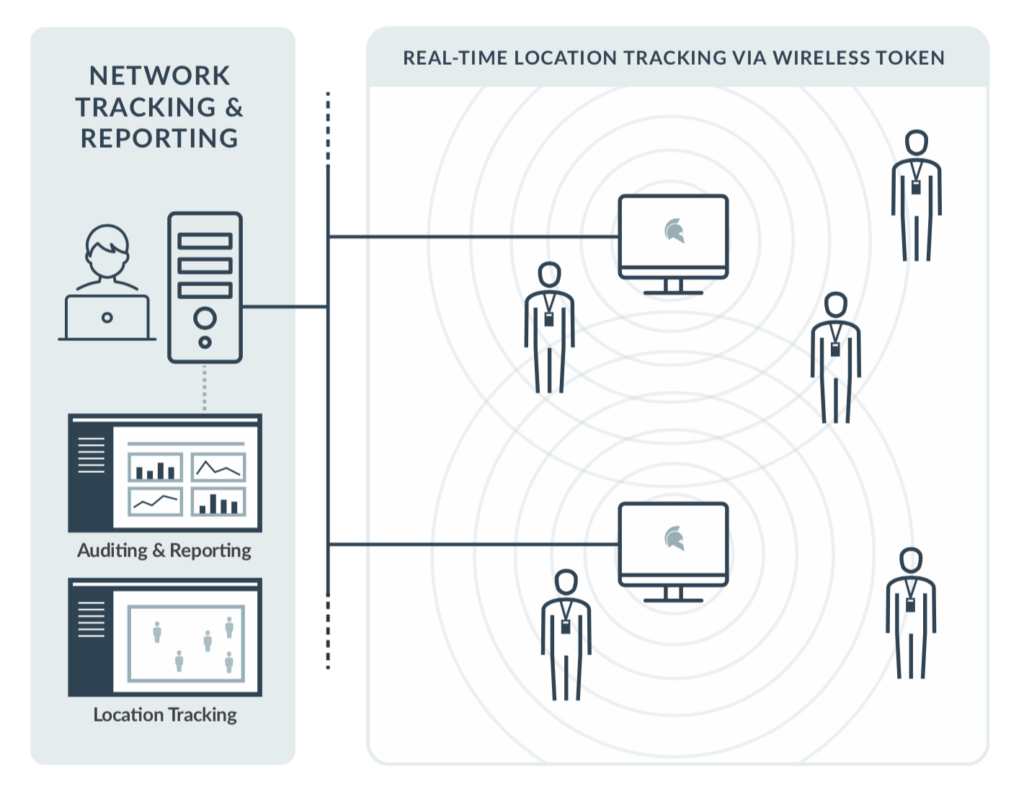
Continuous yet convenient 2FA.
The continuous 2FA token is an access control solution that operates on proximity-based access. Therefore, GateKeeper can lock and unlock your workstation continuously based on the token’s presence. Set your custom distance to lock and unlock workstations faster.
How does it work? The user carries a wireless key small enough to carry on a keychain. When the user walks out of a prescribed range, the device locks automatically. When the user returns to that range, the device unlocks. This provides an additional security system with continuous authentication that creates no extra burden for the user.
The GateKeeper security token can keep you safe from the threat of a malicious attacker getting access to your computer. Use continuous 2FA for the strongest type of authentication. The constant challenge-response mechanism will never stop looking verifying until the token is out of range.
See GateKeeper Enterprise advanced MFA in action.
Take a self-guided tour of how you can evolve from passwords. Then you're really saving time with automation.




