
Preventing Man-in-the-Middle Attacks with GateKeeper.
Prevent man-in-the-middle attacks using GateKeeper 2FA.
Using a 2-factor authentication solution prevents malicious actors from successfully executing a man-in-the-middle attack, even if a password is stolen. The thief would still need the second authentication factor to gain access to the targeted account. Man-in-the-middle attacks involve a malicious actor listening in on communications. A typical example is a phishing attack where the attacker uses the gained credentials from phishing to communicate with the victim’s account and gain access. Therefore, it is crucial to prevent MitM attacks actively.
Preventing phishing attacks on 100 users each with 100 accounts is a lot of ground to secure. However, training is expensive. Awareness takes a disciplined approach to be effective. Those tricky cyber criminals that use domain names so similar to the real thing do succeed enough times to warrant their continued attacks. Remember, it’s all about statistics – at the end of the day, they’ll trick enough victims. Instead, use an enterprise password manager solution to automate the inputting of passwords. This way, if one of the hundred users accidentally clicks a phishing link, the token will not auto-fill any passwords since the site is not approved. After that, no more fooling users by changing a single letter in their bank’s website domain name.
Mitigating MiTM attacks with GateKeeper solution.
GateKeeper Enterprise password manager features multiple safeguards regarding security to prevent internal system intrusion. A read-only device firmware prevents cryptographic key readback if an attacker gains physical access to the token. The tokens only accept over-the-air firmware updates when the firmware is signed by Untethered Labs, Inc. – making it impossible to insert malicious firmware into a token. Also, credentials are encrypted locally using AES 256 encryption.
In order to prevent duplication of GateKeeper tokens and mitigate Man-in-the-Middle (MiTM) attacks, a randomly-generated SECRET KEY can be written to each token after registration. This SECRET KEY is then used to automatically generate one-time passcodes on the token which are sent as part of the Bluetooth advertisement packets and scanned by the GateKeeper Client software over a secure channel. The one-time passcodes modulate every few seconds and therefore, prevents other devices from imitating a GateKeeper token. Prevent MitM attacks by employing a 2FA solution ASAP.
How to mitigate Man-in-the-middle attacks using GateKeeper. |
|
| Set up and use a VPN to login. | Users can seamlessly login to their VPN using a key rather than tediously and repeatedly typing passwords by hand. |
| Protect open websites. | Signing back in is seamless using a token, meaning users can log out of websites without fear of having to sign back in. |
| Prevent phishing attacks. | Most phishing attacks rely on unsuspecting users to give up their login credentials. If the user uses a key, they don’t know the password to give up. GateKeeper only auto-fills on approved websites, so users can automatically avoid phishing sites simply by letting GateKeeper auto-fill passwords. |
| Use 2FA to enhance security. | Using GateKeeper, 2FA is done automatically and users can login faster than ever with fewer steps. |
| Use longer and harder-to-guess passwords for your router, computer, websites, and desktop applications such as EHRs and CRMs. | Using a longer and more difficult-to-guess password is not what people naturally tend to do because it’s more effort to memorize and type. GateKeeper allows long, 50+ character passwords that can take supercomputers centuries to guess. |
| Reducing IT costs by eliminating password resets and forgot password helpdesk tickets. | GateKeeper allows admins to use longer and more secure passwords in place of more frequent password resets. After that, users won’t need to remember any passwords to forget anymore. |
| Eliminating passwords written on paper. | Insecure password written on paper for everyone to see can lead to a malicious actor stealing the credentials. Therefore, avoid this by using a password manager and making passwords too long and complex to write down. |
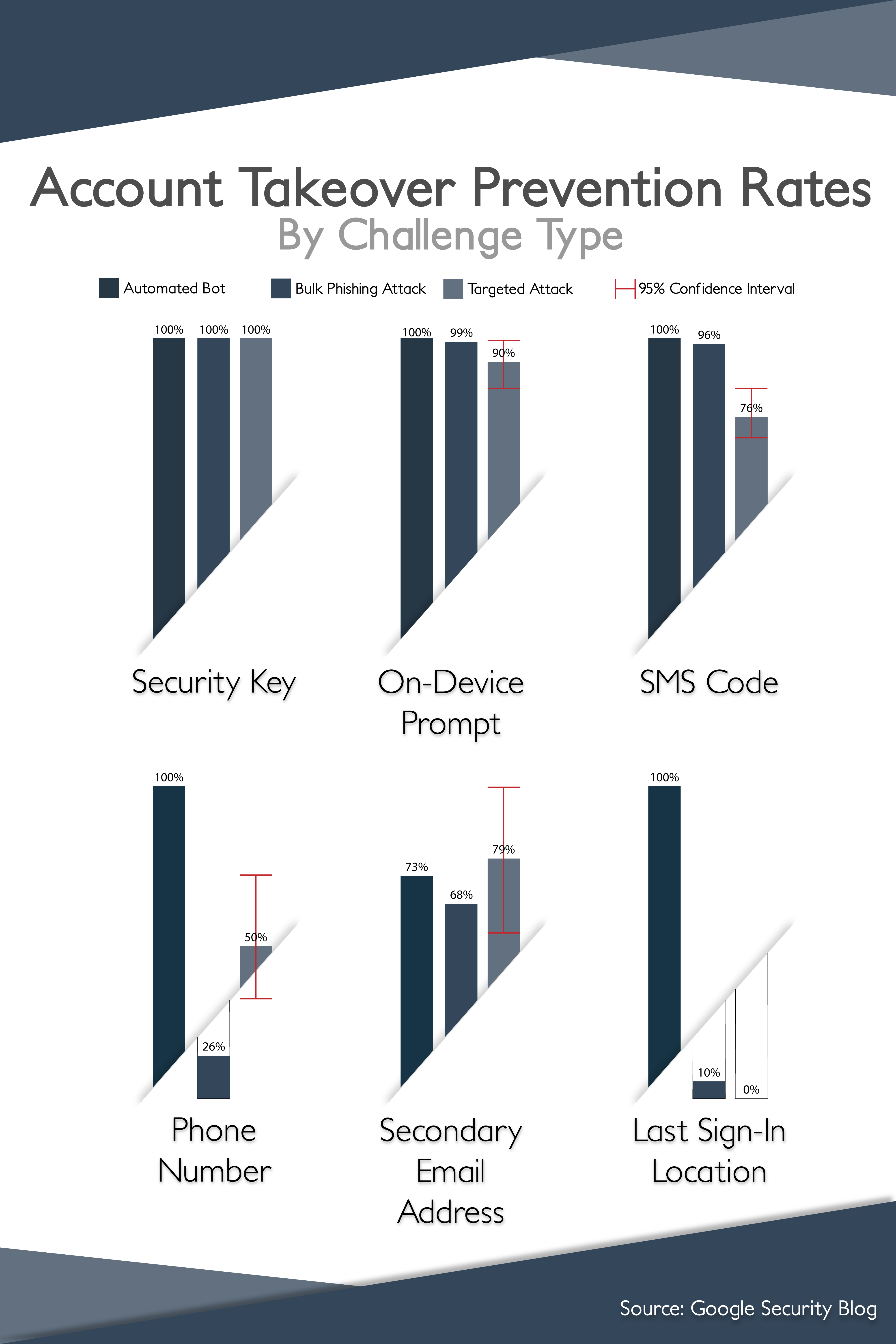
| Avoiding insecure SMS text 2FA. | Research has proven that SMS 2FA is vulnerable to MitM attacks. Using a localized hardware token solution is significantly more secure. A study by Google research determined that no users that exclusively used security keys for 2FA fell victim to targeted phishing during the investigation. |
| Don’t share passwords the insecure way. | Using GateKeeper, users can securely share passwords with other users without the risk of interception through a secure password manager solution. |
See GateKeeper Enterprise advanced MFA in action.
Take a self-guided tour of how you can evolve from passwords. Then you're really saving time with automation.




