Computer-aided dispatch (CAD) systems are utilized by dispatchers, calltakers, and 911 operators to prioritize and record incident calls, identify the status and location of responders in the field, and effectively dispatch responder personnel.
One of the oldest and simplest encryption methods by shifting plain text letters (substitution shift) to avoid them being readable to anyone but the intended parties. This cipher technique was used by General Gaius Julius Caesar in his military campaigns to protect his army's situation, whereabouts, movements, and plans in the 1st century BC.
Cascade login (or "cascading login") is known as a login method that accesses multiple login accounts using one factor. A secure cascade login is similar to SSO but instead of using one's Gmail or Facebook account, the user will use authentication factor (hardware token, biometric).
Catfishing is a type of social engineering where someone creates a fake identity on social media accounts to lure people into emotional or romantic relationships.
The FBI's CJIS (Criminal Justice Information Services) compliance requires any law enforcement agency or other government agency that has access to CJIS databases protect access to that data. Failure to adhere to CJIS compliance could result in loss of access to FBI databases.
CLETS, which stands for the California Law Enforcement Telecommunications System, is a secure computer network that connects law enforcement agencies in California, allowing them to access and share information from various databases.
Clickjacking (or "UI Redressing") is a form of malicious online activity where the victim is tricked into clicking something different from what they perceive.
There are five levels of CMMC. CMMC Level 3 includes the 110 security requirement specifications from NIST SP 800-171. The CMMC Model also incorporates standards from NIST SP 800-53.
Contactless sign-in refers to a process of access control where individuals can authenticate their identity without having to make physical contact with a device or surface.
Continuous authentication is a method of identity confirmation on an ongoing basis. Instead of a user simply being logged in once, the authentication mechanism continues to re-verify the identity of the session user even after logging in. Authentication that continues to challenge is significantly more secure than an authentication system that only challenges once a day.
COWs (Computers on Wheels) and WOWs (Workstations on Wheels) are mobile computer systems designed to bring digital access directly to the point of care, most commonly in healthcare settings such as hospitals and clinics.
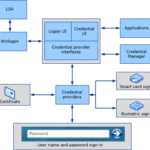
A Credential Provider is a software component, often part of an operating system, that acts as an intermediary between the user interface and the system's authentication mechanisms. It's responsible for collecting and providing user credentials, like passwords or PINs, to the system for authentication.
Assets that the government considers crucial to the security, economy, and/or public health of the country. Presidential Policy Directive 21 (PPD-21) identified 16 critical infrastructure sectors in the US, including healthcare.
Controlled Unclassified Information (CUI) refers to sensitive information that requires safeguarding or dissemination controls according to law, regulation, or government-wide policy, but is not classified under Executive Order 13526 or the Atomic Energy Act. CUI includes information that, while not secret, could still cause harm if improperly released, accessed, or disclosed.
Cyber liability insurance exists to cover costs associated with cyber attacks in the event that your business becomes victim.
Cyber Psychology is the study of how we as humans interact with, and are affected by, technology. It is a field based around what technology can do both for us and to us, and the many ways in which humans take advantage of these factors.
Cyber Resilience refers to an organization’s ability to withstand, recover from, and adapt to disruptions caused by cyberattacks, system failures, or other unexpected incidents. It goes beyond prevention, focusing on maintaining critical operations and minimizing downtime during adverse events. A resilient security strategy includes redundancy, access control, real-time monitoring, and rapid incident response.
Cyber security is the protection of computer and digital systems to prevent unauthorized access and disruption of service. Cyber security involves both the digital and physical security aspects that protect computers and virtual data.
Government organizations must keep up with technological advancements in order to stay on equal footing with allies and enemies. This sentiment has ultimately led to the development of modern Cyber Warfare, where a nation-state or international organization attempts to disrupt or damage another nation's networks by launching cyber attacks.
A cybercriminal gang is a group of individuals or entities involved in digital crime. Cybercriminal gangs have been responsible for more advanced threats with better organization and access to greater resources and funding. Most APTs are executed by either cybercriminal gangs or nation-states.
According to studies, over 30% of all support tickets are related to password resets/forgotten passwords.
Enterprise 2FA and password manager. One key for all your passwords. Experience fully automated login and security. Faster MFA, auto-OTP, password manager, and worry-free workflow with proximity-based privileged access management for Windows 11, 10, 8, 7, VPNs, websites, and desktop applications including MES, EHR, CAD, and more. Overall, a massive upgrade to security and efficiency.
or call 240-547-5446

![[IT WIKI] CAD [IT WIKI] CAD](https://gkaccess.com/wp-content/uploads/2025/06/IT-WIKI-CAD-150x150.jpg)



![[IT WIKI] CLETS [IT WIKI] CLETS](https://gkaccess.com/wp-content/uploads/2025/06/IT-WIKI-CLETS-150x150.png)