Medical Cyber Security with GateKeeper
Medical cyber security automated for doctors and nurses. GateKeeper is a localized wireless tracking solution that allows for constant real-time monitoring of personnel in a pre-determined and well-defined location. Personnel…
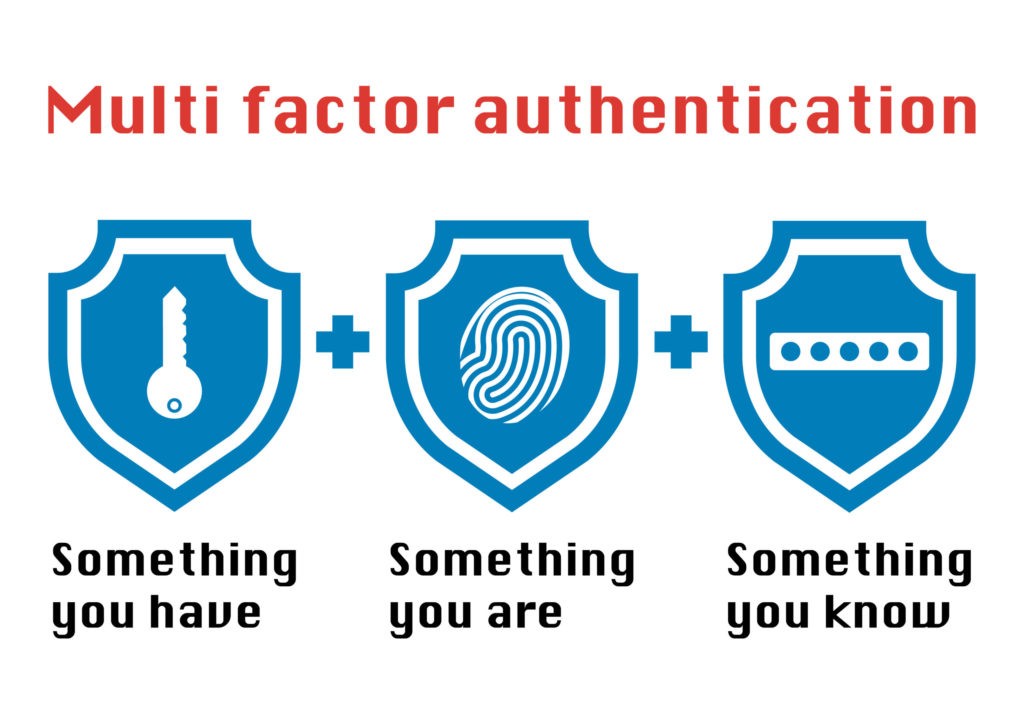
Read MoreWhy Enterprises Should Rush to Adopt Multifactor Authentication.
Phishing attacks, social engineering, database breaches, cyber attacks – all terms that have found their way into our daily lives. If the incessant news of the past decade has shown…
Read MoreContinuous and Convenient 2FA
We all use some form of authentication—passwords, passcodes, an ID card—upon entering into a place with restricted access. Whether this place is digital or real-world, authentication systems are typically founded…
Read MoreTrain and Arm Employees with the Tools to Stave Off Privacy Theft
A 167% growth in ransomware attacks in one year – are you protected? Even the best firewalls can’t prevent every single virus from sneaking into your organization. Ransomware sliding through…
Read More4 Common Ways Attackers can Access a Desktop
Having access to one of your business computers is an attacker’s dream. They not only have access to the desktop’s resources, but they have full access to anything the local…
Read MoreWhat About the Cyber Threat Walking the Floors of Your Hospital?
Every day, there are new reports of cyberattacks around the world striking with increasing reach and devastation. Headlines like “Global ransomware attack hits Merck, health system after thrashing Europe” show…
Read MorePassword Security Rules: Choose Length Not Complexity
You’ve been snoozing that annoying security popup for two weeks and time has run out. Password rules are being broken too often and brazenly. Your password needs updating. Even as…
Read More6 Habits You Need to Break Now If You Want To Avoid a Patient Data Breach
Habits can be hard to break; we get it. Especially when they’re habits we’ve developed at work. We can’t blame clinicians for these bad habits though. They’re just taking on…
Read MoreHow to Find and Ban IPs of Hackers
Dealing with the hackers and malicious visitors is becoming tough day by day. The ease of changing IP addresses and names is giving them freedom to attack different online store…
Read More