Cybersecurity Lessons Learned From Two Years of Remote Work
2020 and 2021 were busy years for the infosec community, overflowing with cybersecurity lessons to remember. It all started in March 2020 when the COVID-19 pandemic disrupted the business and…
Read MoreGateKeeper Proximity Recognized as High Performer in the G2 Winter 2022 Grid® Report for Multi-Factor Authentication (MFA)
The G2 Winter 2022 Grid® Report recognizes GateKeeper Proximity’s high performance across multiple categories. WASHINGTON, D.C., Jan. 17, 2022 / — Untethered Labs, Inc. is proud to announce that the GateKeeper…
Read MoreImprove Efficiency in Dental Offices with Faster Logins
How Faster Authentication and Auto-logouts Help Improve Efficiency in Dental Offices Improved efficiency is always a key goal for dental healthcare providers. However, this cannot come at the expense of…
Read MoreCyber Insurance Providers Require MFA
People are not afraid enough of data breaches. It’s not that people are fearless and undaunted, it just means most people are unaware in this fast, ever-evolving world of cyber…
Read MoreHardware-Based 2FA into PCs
Hardware-based two-factor authentication (2FA) is a powerful security measure that provides an additional layer of protection beyond traditional usernames and passwords. By requiring both something you know (password) and something…
Read MoreWhat DoD Contractors need to do while we wait for CMMC 2.0
The Department of Defense’s (DoD’s) Office of the Under Secretary of Defense for Acquisition and Sustainment recently issued a long-awaited overhaul to its Cybersecurity Maturity Model Certification (CMMC) program. The…
Read MoreBest XyLoc Alternative – GateKeeper Proximity
Looking to lock workstations automatically when users leave? GateKeeper’s “walk-away lock” mechanism maximizes user productivity while increasing computer security. If you’re looking for the best XyLoc alternative, check out the…
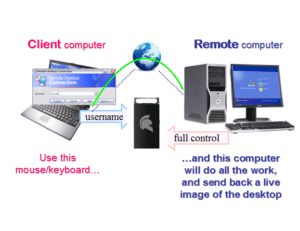
Read MoreThin Client 2FA using GateKeeper Proximity
Thin Client 2FA Access with GateKeeper Proximity. 2FA thin client access is crucial for any good security infrastructure. But protecting access to thin clients and RDP isn’t always straight-forward. The…
Read MoreHow the ENIGMA Cipher was Hacked in World War 2
The iconic ENIGMA machine was widely used during World War 2 by the German military and thought to be uncrackable. But, the incredible story of how the ENIGMA cipher code…
Read More