Software as a Service ("SaaS") is a cloud computing model in which software is provided and used over the internet. In return, this eliminates the need for user owned local servers or computers that must have software manually installed and maintained.
The Saudi Arabian Monetary Authority (SAMA) introduced the SAMA Cyber Security Framework for all banks, insurance companies, and finance companies operating in Saudi Arabia to adhere to.
SCADA (Supervisory Control and Data Acquisition) refers to a system of hardware and software used to control, monitor, and gather real-time data from industrial processes. It plays a central role in managing infrastructure like power plants, water treatment facilities, and manufacturing lines. Because SCADA systems often connect to critical operations, securing access and preventing unauthorized control is vital to ensuring operational safety and reliability.
Often shortened to SecOps, Security Operations describes the practice of integrating secure practices into an organization's daily IT functions. This often requires collaboration between IT security and IT operations networks. As a result, the organization is better postured to prevent, detect, and respond to possible cybersecurity threats in real time.
Security Automation refers to the use of technology to automatically detect, analyze, respond to, and remediate cybersecurity threats without requiring human intervention.
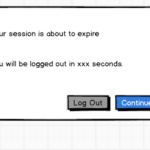
A session is a persistent interaction between a user and a system that begins with successful authentication. It is maintained using a temporary session secret stored in the user’s browser, application, or operating system, allowing continued access without re-entering credentials. Sessions typically end with logout, timeout, or administrative termination to protect against unauthorized access.
Shadow IT is unauthorized hardware, software, or cloud services within an organization that poses potential security and compliance risks.
A shared account is a single login account that is shared between multiple people. Typical examples of shared accounts include sharing a computer login account, email accounts, streaming services. Shared accounts allow multiple users to access a resource that may have only been meant for a single user. In corporate IT security, shared accounts are not in line with best practices due to the lack of accountability and auditability.
A shared workstation is a computer that is accessed by more than one user. Also known as a "kiosk computer". In most cases, workstations in the workplace are shared because of a need to share a certain desktop application login, save cost on licensing per user accounts, or just to save time on logging in.
Shoulder surfing is a social engineering act of looking over a user's shoulder to gain unauthorized data. A prime example of shoulder surfing is watching someone's keystrokes as they type their password. Shoulder surfing can also occur over CCTV camera footage or even by malicious actors using high-powered binoculars.
Security Information and Event Management (SIEM) helps organizations detect threats, ensure compliance, and gain real-time insights by centralizing and analyzing security event data from across their IT environment.
A smartcard is a physical card embedded with an integrated chip that securely stores and processes data for identity verification, authentication, and access control, commonly used in bank cards, NFC-enabled access badges, and secure entry systems.
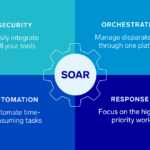
Security orchestration, automation, and response (SOAR) refers to a set of services and tools that automate cyberattack prevention and response. This automation is accomplished by unifying your integrations, defining how tasks should be run, and developing an incident response plan that suits your organization’s needs.
A Security Operations Center (SOC) is a centralized team or function within an organization that focuses on monitoring, detecting, analyzing, and responding to cybersecurity threats. It acts as the central hub for all security-related activities, employing people, processes, and technology to protect the organization's systems and data.
Social engineering is a method of manipulation seeks to exploit people (usually confidential information such as login credentials, bank information, etc.) using social behavior such as trust. Social engineering can happen unknowingly since lying and subterfuge are components used by social engineers in their methods. Mitigating social engineering risks is key to a strong cyber security posture.
A software token ("soft token") is a software-based security token (rather than hardware-based, such as a physical key fob). The software token can be stored on the laptop, desktop, smartphone, or other electronic device.
A supply chain attack is a type of cyberattack that targets a trusted third-party vendor who offers services or software vital to the supply chain. Software supply chain attacks inject malicious code into an application in order to infect all users of an app, while hardware supply chain attacks compromise physical components for the same purpose.
SSO (Single Sign-On) is a method of authentication and access control that grants authorized users access to multiple applications with a single input of their credentials. This central identity management system then allows users to access applications without the need to re-enter their credentials.
Syslog is a standard messaging protocol for sending and receiving event messages on Unix-based operating systems. With it, users receive detailed, formatted information about errors, warnings, and other relevant data generated by the network or connected devices.
According to studies, over 30% of all support tickets are related to password resets/forgotten passwords.
Enterprise 2FA and password manager. One key for all your passwords. Experience fully automated login and security. For example, faster MFA, auto-OTP, password manager, and worry-free workflow with proximity-based privileged access management for Windows 11, 10, 8, 7, VPNs, websites, and desktop applications including MES, EHR, CAD, and more. Overall, a massive upgrade to security and efficiency.
or call 240-547-5446