What DoD Contractors need to do while we wait for CMMC 2.0
The Department of Defense’s (DoD’s) Office of the Under Secretary of Defense for Acquisition and Sustainment recently issued a long-awaited overhaul to its Cybersecurity Maturity Model Certification (CMMC) program. The…
Best XyLoc Alternative – GateKeeper Proximity
Looking to lock workstations automatically when users leave? GateKeeper’s “walk-away lock” mechanism maximizes user productivity while increasing computer security. If you’re looking for the best XyLoc alternative, check out the…
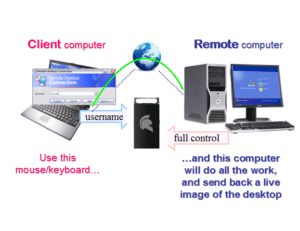
Thin Client 2FA using GateKeeper Proximity
Thin Client 2FA Access with GateKeeper Proximity. 2FA thin client access is crucial for any good security infrastructure. But protecting access to thin clients and RDP isn’t always straight-forward. The…
How the ENIGMA Cipher was Hacked in World War 2
The iconic ENIGMA machine was widely used during World War 2 by the German military and thought to be uncrackable. But, the incredible story of how the ENIGMA cipher code…
How Faster Authentication and Auto-logouts Help Patient Care
In the field of medical care, efficiency and efficacy are paramount. Patients need to receive the very best care promptly — something which will, in turn, reduce costs and improve…
Thin Client Benefits
Modern businesses are constantly on the lookout for ways to improve IT effectiveness and cost-efficiency. IT hardware budgets have fallen on average in the last two years, from 35% of…
History of the Password
The Evolution of the Password Throughout History Every few months, banks, our company’s IT department, email clients and certain apps remind us to change our passwords. And when we do,…
Why Password Change Requirements are Bad
Is your password policy to change passwords every so often? 90 days? According to NIST, the FTC, Microsoft, and other leading organizations, required password changes might be a bad idea…
Reduce Helpdesk Tickets with a Password Manager
Reduce helpdesk tickets with a password manager Is your helpdesk inundated with password problems? According to a study carried out by Google, around 75% of people report experiencing password issues.…