
Security Key – Multi Factor Authentication
Security Key for Multi-Factor Authentication explained.
Hardware-based MFA keys provide an additional layer of security to your computers, website accounts, and desktop application accounts. Security key-based login is an authentication mechanism that uses a dedicated hardware device to grant the user access to a system rather than using a password or other non-hardware based means of verification. Examples of MFA without hardware include SMS text, push authentication, and on-screen behavioral authentication. Research has proven that SMS 2FA is vulnerable to different cyber attacks (like man-in-the-middle attacks).
With a security key-based login solution, the user no longer needs to remember or type a password that may be long, complex, and difficult to remember while staying secure with multi-factor authentication. Therefore, adding a security key is proven to be a very secure method of keeping your password-protected accounts secure because only the true user has the only key able to login (regardless of knowing the account’s password). Just make sure you don’t lose your MFA key. But if you do lose your key, IT admins can instantly disable the lost security token.
Using a physical hardware security key is significantly more secure according to researchers. Moreover, a study by Google Security research and several universities determined that none of the users that exclusively used security keys for 2FA fell victim to targeted phishing during the investigation. Increase cybersecurity posture with hardware tokens.
Proximity-based MFA Key
The GateKeeper Proximity hardware-based multi-factor authentication security key replaces the password and biometric login. Instead, the key gives faster but also secure method of logging in without sacrificing convenience or security. Using proximity authentication, GateKeeper is the fastest MFA login available on the market. The GateKeeper Proximity security token for MFA comes in both hardware token and software token variants.
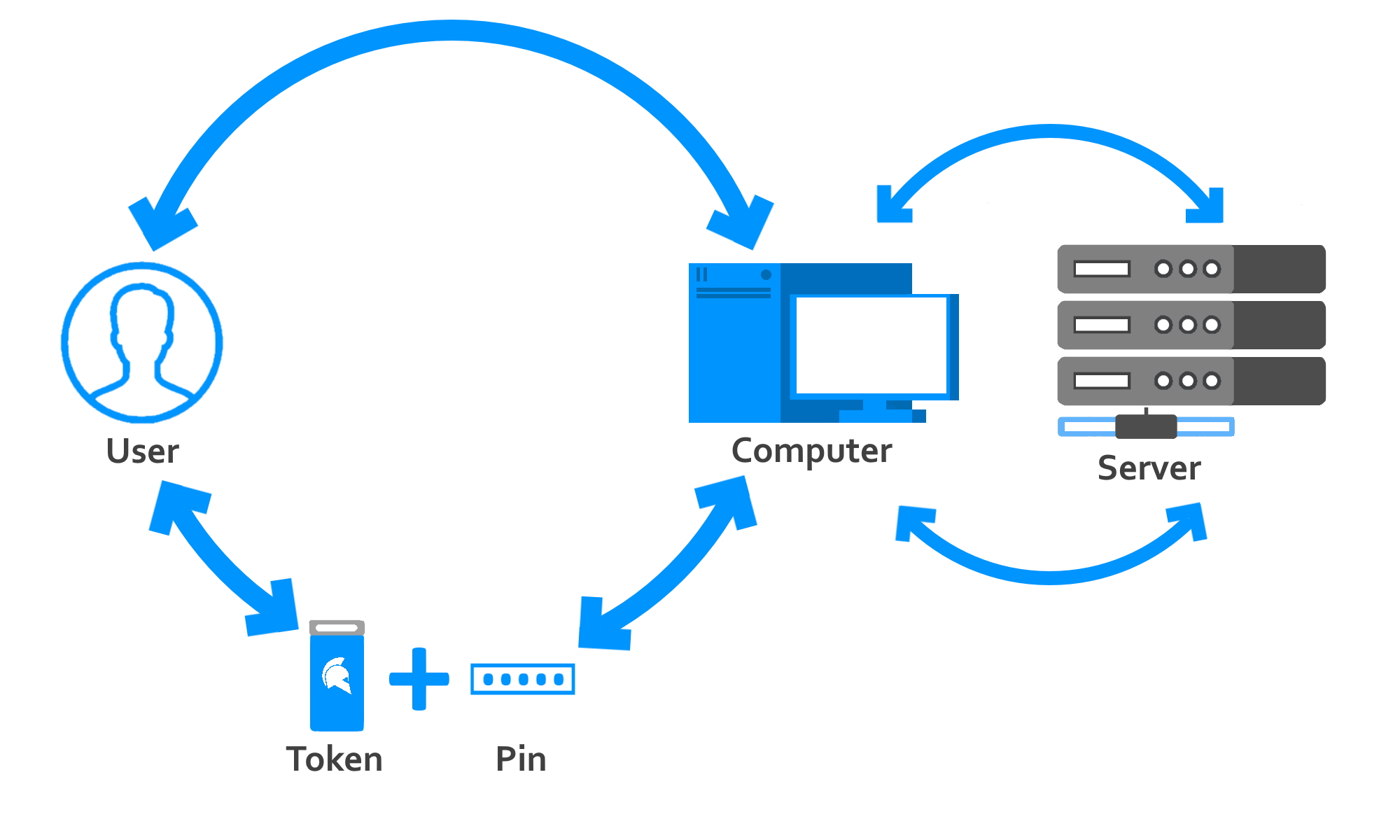
Most security key devices for authentication require manual authentication intent. Examples include typing an OTP code or opening your app on your phone and pushing the authentication button. But the GateKeeper security token works on a wireless, automatic basis. This means faster authentication with minimal to zero human input required. In physical authentication analogy, this is like a person required to have their driver’s license to identify themselves. But then, they are also required to have a badge clearly displayed at all times while in a facility. This is continuous security that requires hardware (IDs).

GateKeeper MFA Token for better security
GateKeeper Enterprise MFA keys features multiple safeguards regarding security to prevent internal system intrusion. Read-only device firmware prevents cryptographic key readback if an attacker ever gained physical access to a token. The keys only accept over-the-air firmware updates when the firmware is signed by Untethered Labs, Inc. This makes it impossible to insert any malicious firmware onto a token. Passwords are locally encrypted with AES-256 encryption.
To prevent token duplication and man-in-the-middle (MitM) attacks, a randomly-generated ‘secret key’ can be written to each token after registration. This ‘secret key’ is then used to automatically generate one-time passcodes on the token which are sent as part of the Bluetooth advertisement packets. The packets are scanned by the GateKeeper software over a secure channel to perform a secure key exchange. The one-time passcodes change on a modulating basis. Therefore, this prevents other devices from imitating a GateKeeper token.
See GateKeeper Enterprise advanced MFA in action.
Take a self-guided tour of how you can evolve from passwords. Then you're really saving time with automation.




