
How to Reduce Cyber Attack Vectors
Cyberattack vector explained.
A cyber attack vector is any way an attacker can gain unauthorized data or access to a system. The attack surface is the sum of all possible attack directions (“attack vectors”) in an environment. There are two types of attack surfaces: physical and digital. But, there are many different attack vectors cybercriminals use to attempt to steal credentials, phish users, gain unauthorized access, plant ransomware/malware, and more. So, it is crucial for IT admins to map out and defend each attack vector.
Reducing cyberattack vectors.
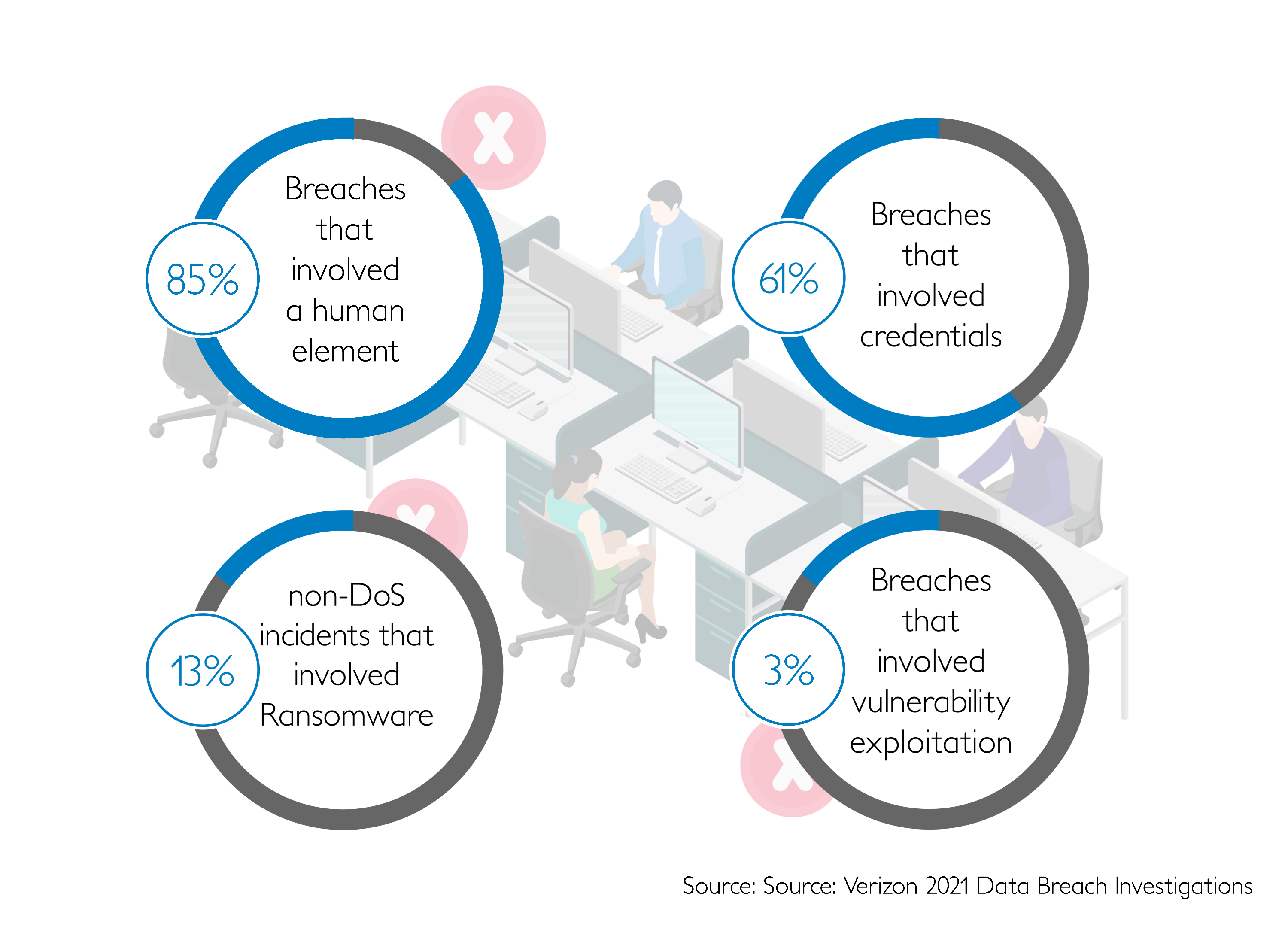
Cyber criminals will exploit as many different vulnerabilities as possible. Some are insider threats, opportunist cyber criminals, while others are professionals using Advanced Persistent Threats. This means they are actively seeking to widen the attack vectors available. Some examples of attack vectors in cyber security are listed below. Each example has a different attack vector and requires specific ways to prevent cyber attacks and defend against them.
- Firstly, weak passwords that are easily guessed or cracked by brute-force attacks. So make sure to use strong passwords and 2FA.
- Unwitting employee clicks downloads an email attachment with a virus. Please make sure your employees are cyber aware and trained.
- Phishing invitation in emails from seemingly trustworthy sources.
- A password a user reused that was already previously compromised. Prevent threats from recycled passwords by using a password manager.
- A shared password with a friend who carelessly let someone else see it. DON’T share passwords.
- Credential stuffing attacks: cyber criminals already knows your username and utilizes a brute force program to test as many combinations as possible to guess your account’s password. So, again, don’t reuse passwords!
- Criminals know that certain products come with known default passwords and users will inevitably forget to change them. Change passwords.
- Cyber criminals are even targeting computing resources with crypto miners.
More attack vectors with physical factors.
- Unlocked computers that are unattended.
- Passwords written on paper gets lost and then found by an opportunistic criminal. Stop employees from writing passwords down on paper or Excel.
- Shoulder surfing your password in public areas like coffee shops, airplanes, and more. Don’t let people see you type your password.
- Cybercriminals shoulder surfing your password from hacked or even public CCTV camera footage. Watch your back…
- Malicious insiders opportunistically waiting for another user to leave a computer unlocked to gain unauthorized access.
- Criminals using a keylogger to steal your username and passwords.
- Vishing scam phone calls that utilize social engineering to convince the user to give up confidential information unwittingly. Afterwards, they will use the stolen information to break into back accounts and more.
- Infected USB sticks with malware preloaded onto them as a trap. So, make sure you don’t pick up random USB sticks and plug them in.
- Someone breaks in and installs malware or a keylogger.
- Stolen laptops, lost phones.
- Researchers have even shown that programs can use the sound of your keyboard clicks to determine the user’s password. In conclusion, the attack vectors are almost endless.
Reduce attack vectors drastically.
GateKeeper™ Proximity reduces the attack vector of cyber criminals by requiring a local-proximity, hardware-based automatic 2FA login mechanism. With so many different possibilities of attack, the logical defense was to nullify as many attack vectors as possible and reduce potential attack vectors down to as few as possible.
So, with a hardware-based, local-only token login method, IT admins can more effectively and easily protect computers and users from many different attack vectors by requiring the user to be in front of the access terminal itself to login. Afterwards, attackers can no longer gain unauthorized access simply by attaining stolen passwords. With longer, harder-to-guess passwords in place for all accounts, IT admins can easily protect every end point. End users will also be able to login without typing any of the long passwords by simply having a proximity key on them. With dynamic login options available, IT admins can enforce security while end users login seamlessly.
Learn to avoid common mistakes that plague organizations.

See GateKeeper Enterprise advanced MFA in action.
Take a self-guided tour of how you can evolve from passwords. Then you're really saving time with automation.




