What is Data Encryption?
Data encryption in cybersecurity is a conversion of data from readable form into encoded format. This data is useable only when it is decoded with a unique decryption key which is usually generated before or during the encryption. Data encryption is a building block of data security and there is hardly a network system that does not use this technique. Encrypted data and messages are vital to a strong cyber security posture.
The encrypted data, also known as ciphertext, appears unreadable to unauthorized users. The encryption system is used in conjunction with the authentication services to ensure the decryption keys are provided to only authorized parties.
Over the years, data encryption has proved to be the easiest and simplest way to ensure the security of data during storage and transmission and make sure it’s not stolen and read by someone without permission. One of the earliest examples of encryption is the Caesar Cipher, used over 2,000 years ago by General Gaius Julius Caesar. Another example is the Enigma machine from the second World War.
Scope of Data Encryption
Data encryption is a primary line of defense against cyberattacks. The aim is to prevent cyber criminals from accessing sensitive data and using it for malicious purposes. The data algorithm software, also known as a cipher, develops an encryption architecture that, in theory, is significantly more difficult to be bypassed by unauthorized parties.
In modern cybersecurity, almost every type of data is protected by encryption, ranging from personal credit card transactions and small local firms to larger corporation and government intelligence data. Encryption should be end to end, at all points possible.
Types of Data Encryption
Data encryption is usually classified into two broader categories:
- Symmetric
- Asymmetric
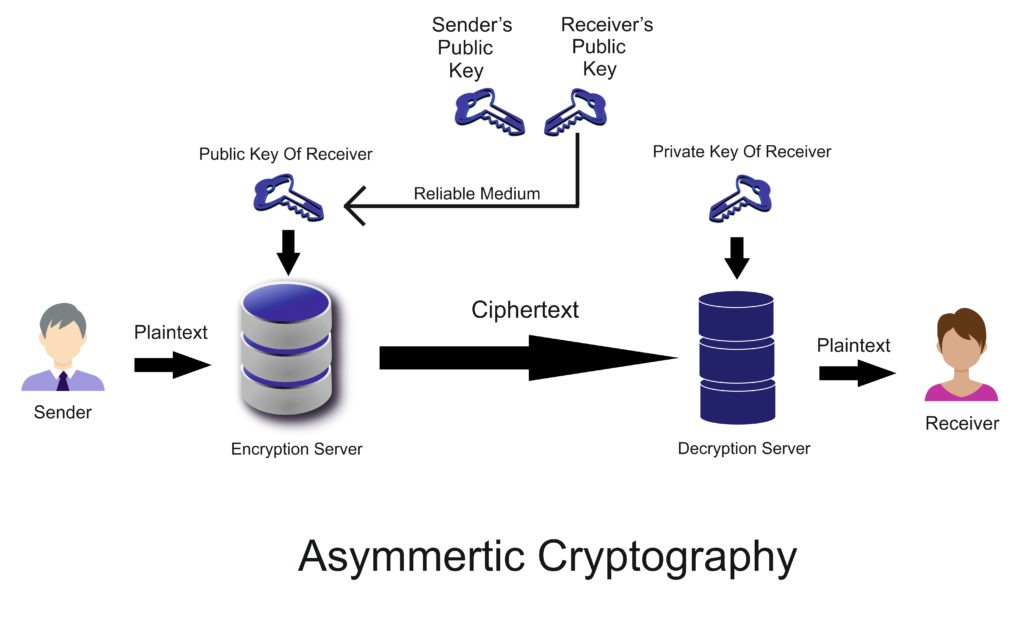
Symmetric encryption uses the same key to encrypt and decrypt data. Most small data sets use this method because of its high speed. Asymmetric encryption, on the other hand, uses two different keys, one private and the other public, to encrypt and decrypt the data.
The encryption key is public and can be used by anyone while the decryption key is private and used by only authorized users to decrypt. Both types have their own benefits but in general, asymmetric encryption is more secure than symmetric, albeit slower.
Challenges of Data Encryption
Companies should always be on their toes to ward off the latest cyberattacks. The biggest threat to data encryption comes from brute force attacks. A hacker will try as many passwords combinations as possible until the right one is found.
Similarly, cybercriminals use side-channel attacks and cryptanalysis to exploit the vulnerabilities in the encryption algorithm or cipher and find out the decryption key. These attacks occur due to the flaws or security laps in the cipher itself.
Enterprise 2FA and password manager. One key for all your passwords. Experience fully automated login and security. Faster MFA, auto-OTP, password manager, and worry-free workflow with proximity-based privileged access management for Windows 11, 10, 8, 7, VPNs, websites, and desktop applications including MES, EHR, CAD, and more.
or call 240-547-5446

